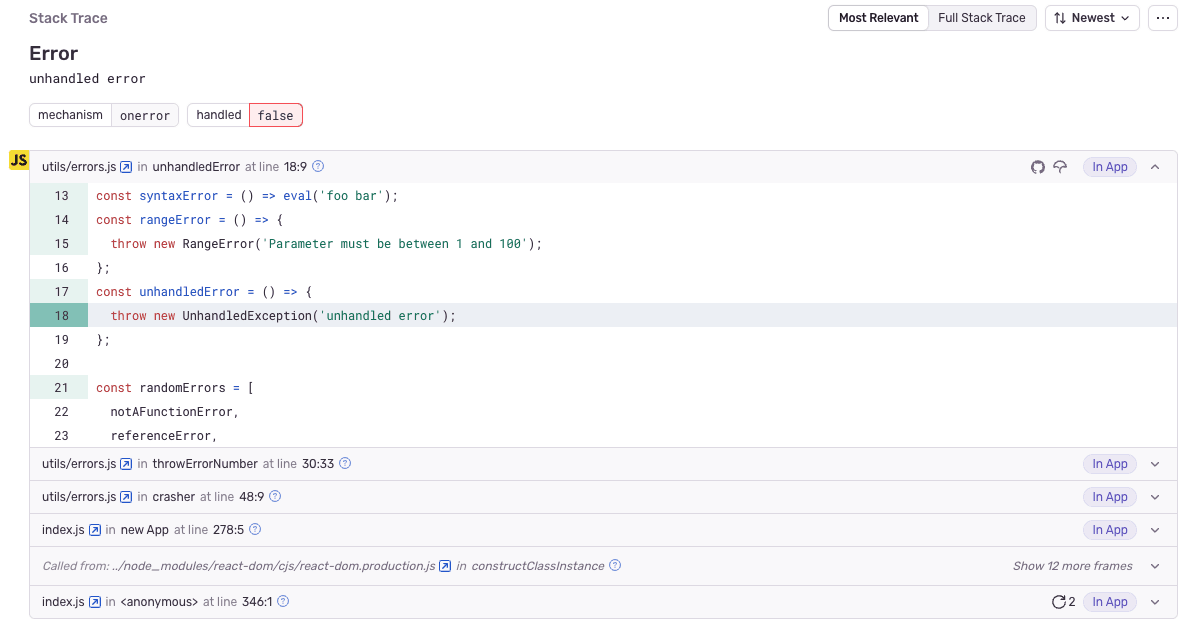
Like stack traces,
but more and better
Stack traces, also referred to as a backtrace, are often used to debug or troubleshoot. Sentry enhances stack traces with all the information you wish they had to enhance debuggability.
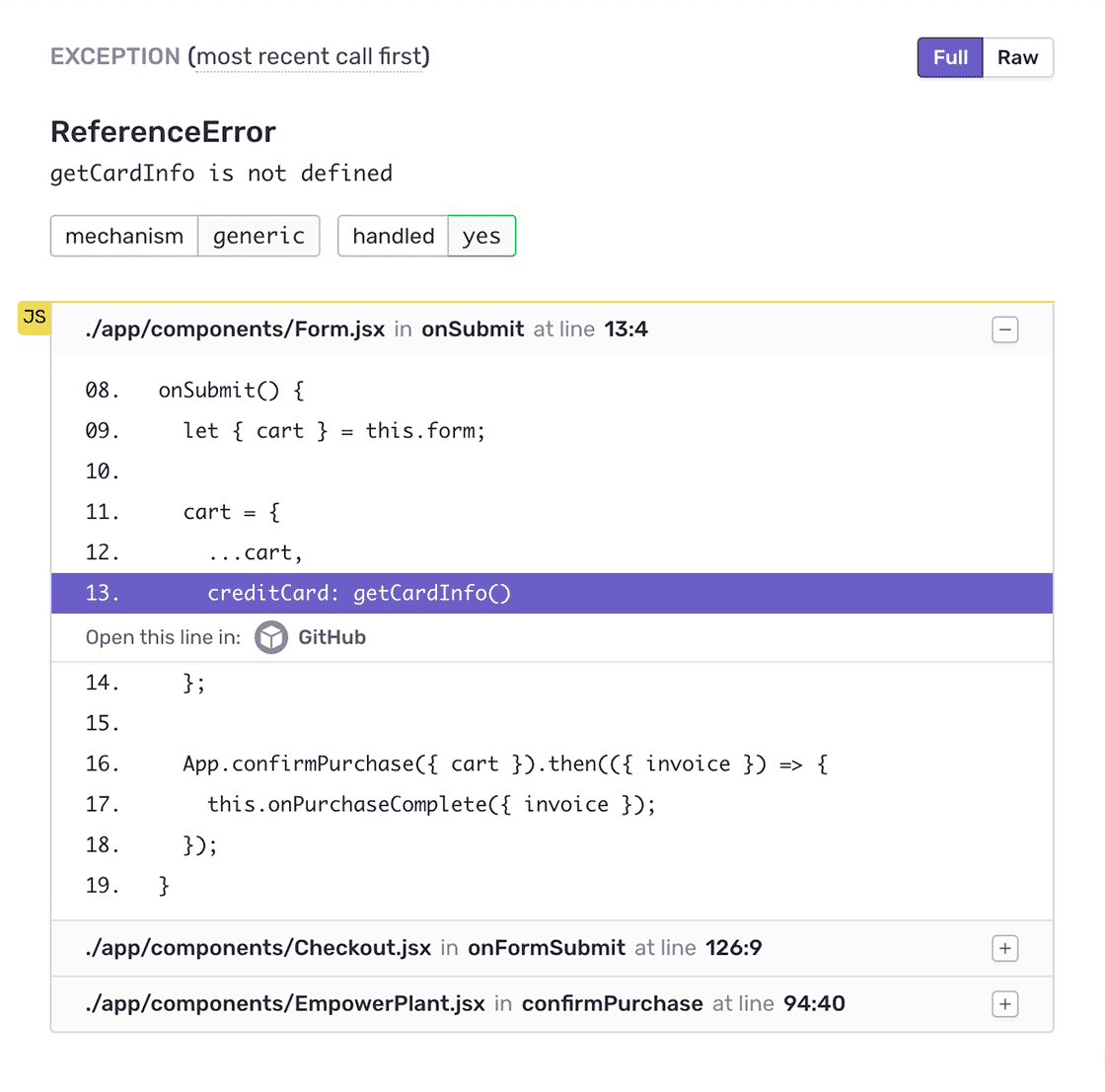
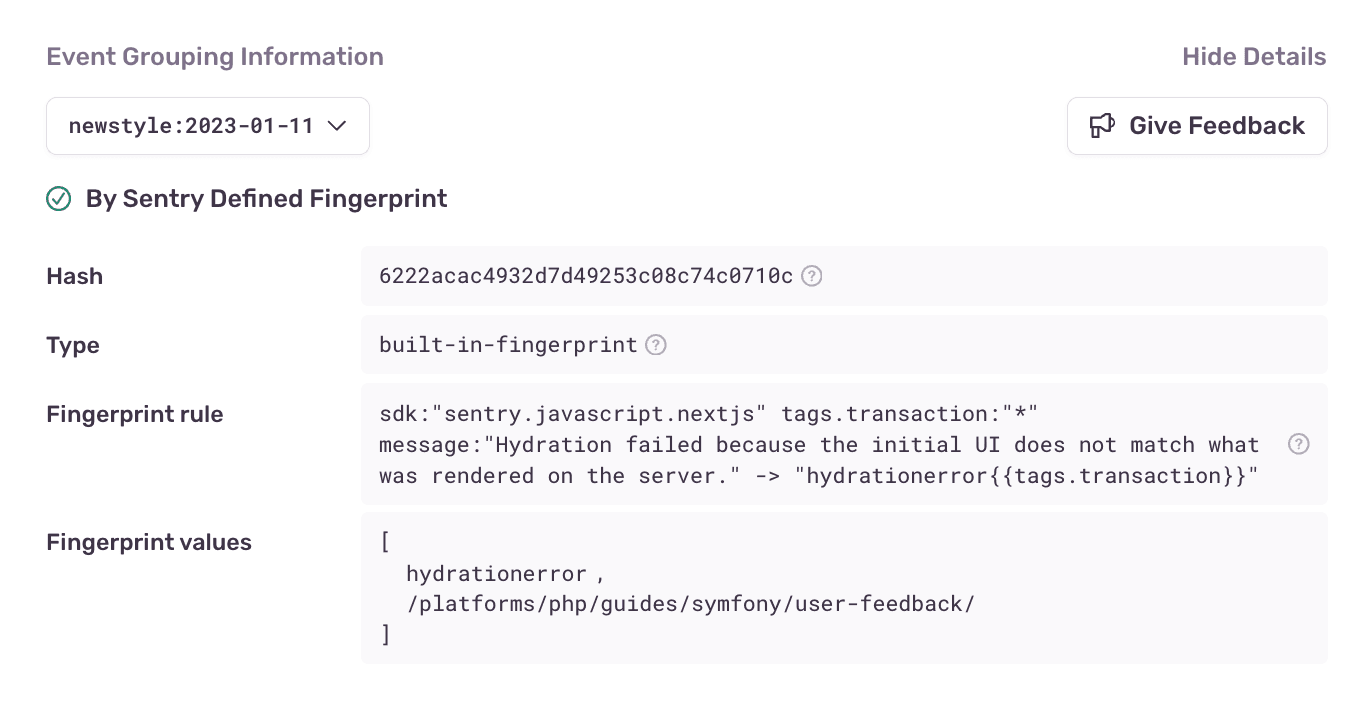
Issue filters
To reduce noise, Sentry groups related issues by analyzing stack traces, exceptions, and messages, surfacing the most critical issues. Plus, you can update filters to focus on application-specific errors, include framework errors, or show the raw trace for deeper debugging.
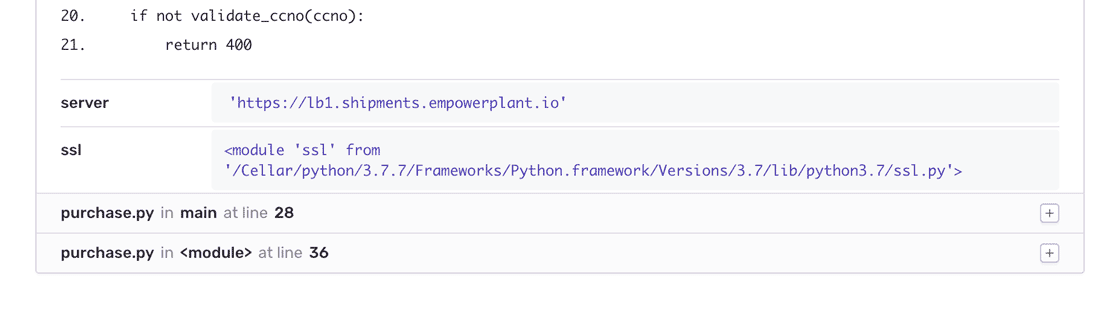
Stack locals
For Node, Python, PHP, and Ruby you can see the exact value of each variable at the time of the crash or error.
Compression got you down?
Sentry can show your source code even if it has been minified, compiled, transpiled, or beguiled.
Sensitive data scrubbing
We automatically scrub things that include personal information, such as credit cards, passwords, or api_keys.
You can also specify custom values to scrub and filter data on the client side before it gets sent to us.